Part 1
Protocol Reference Model
The OSI reference model was developed my the IEEE 802 committee. The lowest level is the physical level and includes such functions as:
Above the physical layer is the data link layer. It provides services to LAN users:
The first function is provided by the sub-layer of the Data Link Control layer, called logical link control layer (LLC) . The functions 2-4 are provided by the sublayer called medium access control (MAC). This is done because for the same LLC, several MAC options may be provided. MAC is topology dependent whereas LLC is not.
Logical Link Control
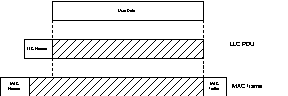
LLC is concerned with transmission of link-level protocol data unit (PDU) between two stations. LLC has specific characteristics:
See figure 4.2, page 142.
LLC provides three fundamental services ( and one optional):
Connectionless service requires source and destination address in the PDU ( the self-containing nature of the connectionless service).
Connection-oriented and multiplexing services require the Service Access Point (SAP) addressing. This concept is similar to the concept of a port in TCP/IP. See figure

Addressing
Communication involves three agents: processes, stations and networks.There are multiple stations on the network and within each station there are multiple simultaneous applications running. For example, file transfer, remote terminal station, etc. The communication between two application consists of first, getting the message to the destinations machine, and second, getting the message to the right application within the machine. (See figure above)
This type of communication requires two levels of addressing. LLC user data is passed down to LLC, which appends a header. The header contains the control information that is used to manage the protocol between the local LLC entity and the remote LLC entity. The LLC PDU is further passed down to the MAC sublayer. The MAC sublayer appends both a header and trailer, to manage the MAC protocol. MAC-level PDU is called a frame.
The MAC header must contain a destination address that uniquely identifies a station on the LAN. When a MAC frame is captured, the destination MAC entity strips off the MAC header and trailer and passes the resulting LLC PDU up to the LLC sub-layer. The LLC header must contain a destination SAP address so the LLC can determine to who the data are to be delivered.
To support multicast, there is a need for a group address. The group address specifies one or more machine. See figure 4.5 on page 128 for different permutations of MAC and LLC addresses.
Medium Access Control
MAC controls access to the transmission medium to provide and orderly and efficient use of that capacity. Control may be exercised in the centralized or distributed fashion. In a centralized scheme a central controller grants access to the network to other machines. In a distributed scheme, stations collectively perform a medium access control function to determine the order in which stations transmit. The advantages of the centralized scheme are:
Disadvantages:
Access control techniques can be synchronous or asynchronous.
Synchronous: specific capacity is dedicated to a connection. This is the same approach used in circuit switching, FDM, synch TDM. Not optimal for LAN and MAN because of the bursty and unpredictable traffic pattern.
Asynchronous: round robin, reservation, and contention.
Round robin: each station takes a turn to transmit. Each station that decides to transmit may transmit up to a specified upper bound (either data or time). This technique is efficient under heavy load (lots of traffic). It is wasteful otherwise.
Reservation: well suited for stream traffic (voice, bulk file transmission). Very similar to synchronous TDM. A station wishing to transmit reserves future slots for an extended or even indefinite period.
Contention: well suited for bursty traffic (remote terminal connection). Stations contend for time in a distributed fashion (collision, backoff). Good under light load, collapses under heavy load.
Prev
Next